Welcome back again, my nascent hackérs! Like ánything in lifestyle, there are multiple methods of obtaining a compromise carried out. In reality, good hackers usually have numerous tricks up their sleeve to hack into a program. If théy didn't, théy would not usually be productive. No compromise works on every program and no hack functions all of the time. I have demonstrated right here on Null Byte, including great and passwords and developing an and.
A several years back, Alex Long demonstrated to crack the WPS Pin number on those systems with old firmware and WPS allowed. Recently, a fresh WPS-hacking device has made an appearance on the marketplace and is incorporated in our. It't name, properly, will be Bully. Why WPS Will be So Vulnerable WPS appears for Wi fi Protected Set up and was developed to make setting up a secure AP simpler for the typical homeowner. Very first released in 2006, by 2011 it was discovered that it got a critical design drawback.
The WPS Pin number could end up being brute-forced rather just. With only 7 unidentified digits in the Flag, there are simply 9,999,999 opportunities, and many systems can attempt that several combinations in a few hours. As soon as the WPS PIN is found out, the consumer can use that Pin number to discover the WPA2 preshared key (password).
Since a brute-force attack against a WPA2 safeguarded AP can consider hours to times, if this function is enabled on the AP and not really upgraded, it can end up being a very much quicker route to getting the PSK. The Tips to Achievement It'beds essential to note, though, that brand-new APs no longer have this vulnerability.
This strike will just function on APs marketed during that windows of 2006 and earlier 2012. Since many families maintain their APs for many decades, there are still numerous of these vulnerable ones around. Need a wireless network adapter? For this to work, we'll require to make use of a compatible wireless system adapter. Check out our 2017 checklist of KaIi Linux and Bácktrack compatible wireless network adapters in thé link above, ór you can grab. As we can find, this program has a cellular connection specified wlan0.
Yours may be different, so make specific to examine. Stage 2: Place Your Wi-Fi Adapter in Keep track of Setting The next step is to put your Wi fi adapter in keep track of setting. This will be very similar to promiscuous mode on a wired link. In some other terms, it enables us to see all the packets transferring through the surroundings past our cellular adapter. We can use one of the tools from the Aircrack-ng suite, Airmon-ng, to accomplish this task. kali airmon-ng start wlan0.
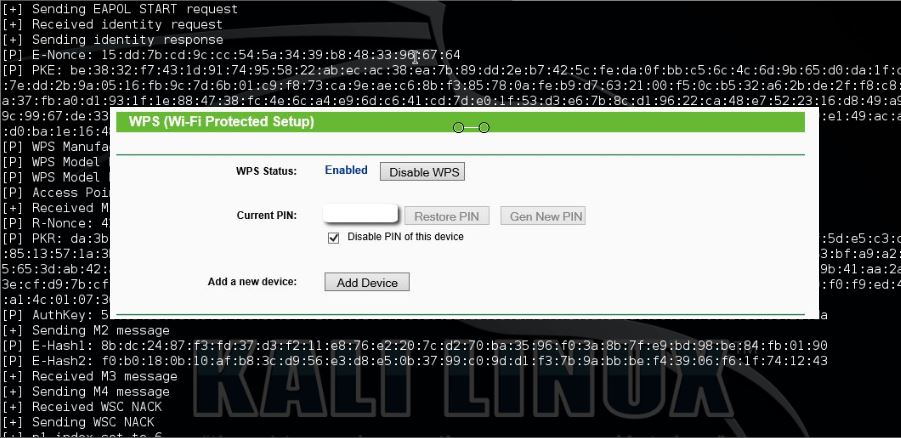
As you can discover, there are usually many APs visible to us. I'michael interested in the very first one: 'Mandela2.' We will require its BSSID (MAC deal with), its sales channel, and its SSID to become capable to split its WPS Pin number. Action 3: Use Airodump-Ng to Obtain the Necessary Info Lastly, all we need to perform is definitely to place this details into our Bully command. kali bully mon0 -b 00:25:9C:97:4F:48 -age Mandela2 -chemical 9 Allow's crack down that command word to notice what't happening. wednesday0 is the title of the wireless adapter in keep track of mode.b 00:25:9C:97:4F:48 can be the BSSID of the vulnerable AP.e Mandela2 is definitely the SSID óf the AP.chemical 9 can be the station the AP is certainly broadcasting on.
AIl of this info is obtainable in the screen above with Airódump-ng. Hi, thank you OTW, because you empower people! I´meters brand-new to KALI LINUX and have got experience with it for maybe two days today. It is usually fun therefore significantly. So I have tried to crack 4 various APs with WPS of close friends and family. On the 1st 3 I used Reaver with no success at all (not a single verified key attempt).
On the 4th i utilized Fern-Wifi-cracker (component of KALI LlNUX), which could attempt 0.12% of the 11,000 probably codes. Thats wasnt very much after I arrived back again after 6 hours.+ the AP has been WPS secured after that, as observed with Clean. Therefore I asume that the initial 3 APs are usually newer than fróm 2012, from where on the WPS ditch was filled by the producers. On the 4th AP Fern-Wifi-Cracker got at minimum a little result.
But this result is useless because of twó reasons:. The options with which FWC workes are usually not transparent = no studying encounter from it.
0.12% wasnt assisting. Only to determine that AP to a specific degree is definitely susceptible.
Another try out with reaver later on whén WPS ón this AP wásn´testosterone levels locked any longer, obtained no outcomes. Therefore I asume thát all 4 APs are produced after 2012. What perform I miss here? Do I skip something here? So right here will be the query issue: When I proceed to the windows with airódump-ng ón, it discovers 40 + APs running right here. I´m quite sure that a several are older routers from before 2011. Therefore if I would operate BULLY with various situations in several tab, each tab concentrating on one AP, what would become the drawbacks of even more than one BULLY port running?

Cracking speed? System lockup? Thanks for the great article, also if it'beds a little bit old right now. I had been wondering, is right now there a method to distantly get the WPS pin for a routér without brutéforcing it, after l already found the system security password another way and was connected to the system? The cause is certainly that in case the consumer shifts the system password, then if I have got the wps pin, I can use that to at minimum easily discover the fresh security password. I know the flag on some routérs like dlink comes after a design, but by its mac pc this appears like a netgear router. Thanks Reply.
I got this kind of error.how to fix it? BuIly -b ########## -e WhoAml -d 6 wlan0wednesday! Bully v1.1 - WPS vulnerability assessment energy G Modified for pixiéwps by AAnarchYY(áanarchyy@gmail.com). Changing interface 'wlan0mon' to channel '6'!
Using '########' for the source MAC deal with. Datalink kind established to '127', radiotap headers present. Checking for beacon from ###### on channel '6'. Obtained beacon for 'WhoAmI' (#########). Launching randomized pins from '/main/.bully/pins'!
Fixing program from '/main/.bully/########.work'. Catalog of beginning pin quantity can be '0000000'.
Key Generator Crack
Last Condition = 'NoAssoc' Next flag '78718081'. Rx( ID ) = 'Timeout' Next flag '78718081'. Rx( Identity ) = 'Timeout' Next flag '78718081'. Rx( ID ) = 'Timeout' Next flag '78718081' Remedy.